Browsing in a private and secure manner is no easy task. There’s always a certain possibility of data leaking and hackers getting your information. Even websites can gather information about you, or your service provider may block certain connections. However, the new ECH protocol will provide a safe and private experience according to its developers. The ECH works in Chrome and it’s a new approach to the browsing experience.
ECH stands for Encrypted Client Hello. It’s an extension of the TLS protocol. HTTPS encrypted websites use it for a more private and secure experience. The service provider can’t use the filtering system when ECH is active. The latest Google Chrome update integrated this protocol and it’s also supported by Firefox. Therefore, the two most widely used browsers are compatible with this TLS protocol extension that will be crucial for maintaining connection privacy.
ECH browsing experience, safety and privacy
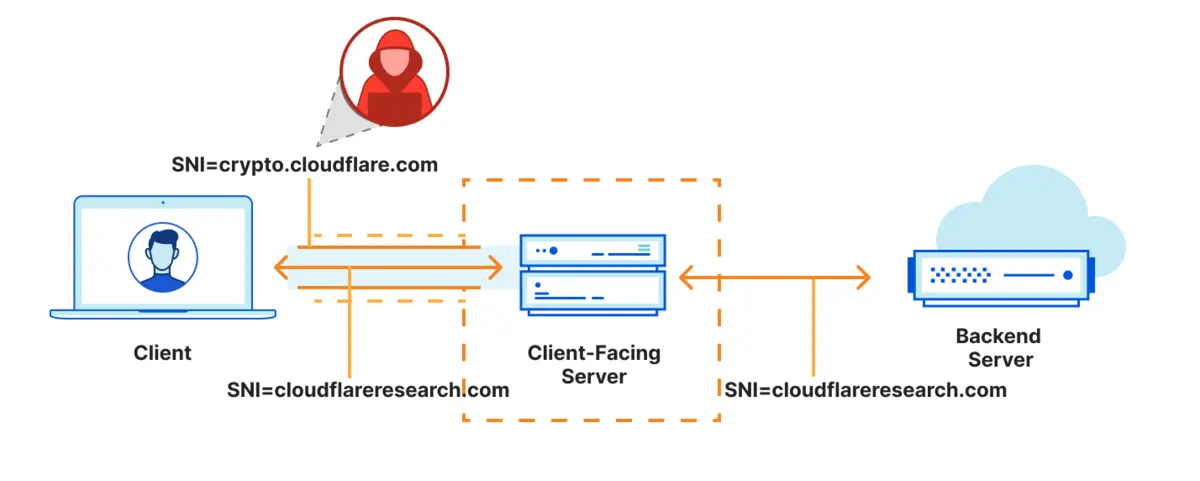
Cloudflare recently announced the activation of ECH across its network. By combining this with Chrome use of the protocol, it will make Internet browsing experience more private and secure thanks to ECH. Until now, TLS had the unencrypted SNI field. This allowed service providers to use filters in order to prevent access to certain websites. In order to protect the SNI, Cloudflare incorporated the eSNI in 2019.
However, this didn’t last long as it was replaced by ECH two years later. During this period, the service provider had an easier time blocking the user connections. For example, they can block sites that broadcast pirated content like sports events.
At the moment, even though ECH keeps evolving, Cloudflare’s announcement of activation across its network is really significant. Combining it with Google Chrome’s support, a page hosted on Cloudflare, whether on the free or paid version, will avoid blocking. Until now, using a VPN was the only option. But not everyone knows how to configure it correctly and ultimately, errors arise. Now, thanks to ECH, the browsing experience will indeed be genuinely private and secure. ECH fully encrypts the ClientHello message using the client server’s public key.
Through the TLS extension, comes a turning point because neither TLS 1.2 nor the TLS 1.3 has natively resolver the SNI issue. Instead, we have an entirely option extension for the best possible privacy. All websites should enable ECH so that they cannot be blocked in transit, as is currently happening when trying to access a website blocked by LaLiga or LaCoalición, for example.
Service providers and the SNI browsing experience against ECH
What other options do service providers have to view the SNI of a connection and potentially block it? They use DPI systems. Essentially, there’s a list of websites emitting pirated content that can be blocked. Service providers resort to packet inspection to obtain the SNI. When they detect an irregularity, the access is restricted. However, they can also opt for DNS blocking, though it’s less popular. There are hundreds of blocked pages around the world. When someone wants to enter, an error message displays.
LaLiga and La Coalición in Spain see ECH as a risk. The users will be able to enjoy a more secure and private browsing experience but it will be more difficult to obtain SNI and block websites. Those sites hosted behind Cloudflare won’t be blocked.
This is great news for freedom in the Internet as well as privacy and security. It will prevent third-party entities like service providers from inspecting traffic and blocking your access to certain websites. In the past, we could bypass these blockades with VPN services like Cloudflare’s WARP or Google One’s VPN. Both services allowed encrypted connections point-to-point and access to INterent through their servers. The use of a third-party VPN service will also help bypass these restrictions without any issue and even evade geolocation filters that some websites might have.